This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Category:OWASP Application Security Verification Standard Project Proposal
Click here to return to OWASP Projects page.
Click here to see (& edit, if wanted) the template.
| PROJECT INFORMATION | |||||||
|---|---|---|---|---|---|---|---|
| Project Name | OWASP Application Security Verification Standard Project | ||||||
| Short Project Description |
The primary aim of the OWASP Application Security Verification Standard (ASVS) Project is to normalize the range in the coverage and level of rigor available in the market when it comes to performing application security verification using a commercially-workable open standard. This standard can be used to establish a level of confidence in the security of web applications and web services. | ||||||
| Key Project Information | Licensed under Choose here & replace link with license name |
Project Leader Mike Boberski |
Project Contributors Jeff Williams Dave Wichers |
Mailing List Subscribe here Use here |
Reviewers Jeff Williams Pierre Parrend |
Roadmap Please see here. |
Sponsors OWASP SoC 08 Aspect Security Booz Allen Hamilton |
| Release Status | Main Links | Related Projects |
|---|---|---|
| Alpha Please see here for complete information. |
About OWASP ASVS: Powerpoint. |
If any add link |
Overview
What is ASVS?
Whereas the OWASP Top Ten is a tool that provides web application security awareness, the OWASP Application Security Verification Standard (ASVS) is a commercially-workable open standard that defines ranges in coverage and levels of rigor that can be used to perform application security verifications. It is the very first standard that OWASP has published! There are currently versions only in English.
The primary aim of the OWASP ASVS Project is to normalize the range in the coverage and level of rigor available in the market when it comes to performing application security verification using a commercially-workable open standard. This standard can be used to establish a level of confidence in the security of web applications.
Where did ASVS come from?
The OWASP ASVS project is led by Mike Boberski (Booz Allen Hamilton). The primary authors are Mike, Jeff Williams (Aspect Security), and Dave Wichers (Aspect Security). The ASVS is the result of the collection and consolidation of decades of collective subject matter expertise in application security. If you’d like to volunteer to help on the project, you can contact Mike at boberski_michael[at]bah.com.
More information about the ASVS can be found here - OWASP ASVS Project's PowerPoint Presentation.
Announcements
- 12/8/2008 - OWASP ASVS Final assistance required! Please join the mailing list for more information and assignments.
- 12/5/2008 - OWASP ASVS exits the Summer of Code 2008! The Beta draft of the Web Application Edition is released! Mike Boberski, Jeff Williams, and Dave Wichers are the primary authors.
- 10/3/2008 - OWASP ASVS Alpha draft is released! Mike Boberski is the primary author.
- 4/16/2008 - OWASP ASVS Summer of Code 2008 proposal submitted by Mike Boberski wins!
Methodology
How does ASVS work?
The OWASP ASVS standard uses the term the ‘verifier’ to indicate the person or team that is reviewing the application against these requirements.
It is a verifier’s responsibility to determine if an application meets all of the requirements at the level targeted by a review. If the application meets all the requirements for that level, then it can be considered an OWASP ASVS Level N application, where N is the verification level that application complied with.
If the application does not meet all the requirements for a particular level, but does meet all the requirements for a lower level of this standard, then it can be considered to have passed that level of verification.
The OWASP ASVS defines verification and documentation requirements that are grouped on the basis of related coverage and level of rigor. Web application security verification is performed from a logical point of view by following (or attempting to follow) paths into and out of the application and performing analysis along those paths. The Standard defines four hierarchical levels (e.g., Level 2 requires more coverage and rigor than Level 1) as depicted in the figure below.
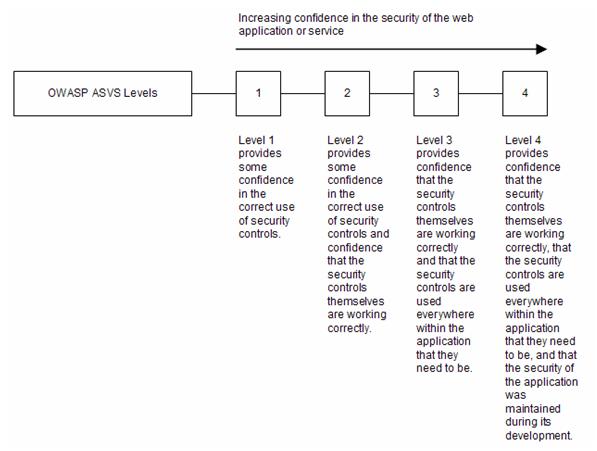
|
The Standard further defines constituent components for Levels 1 and 2 (e.g., verification at Level 1 requires meeting both Level 1A and 1B requirements). Applications may claim compliance to either Level 1A or 1B instead of Level 1, but making such claims is weaker than claiming Level 1. Similarly, applications may claim compliance to either Level 2A or 2B instead of Level 2, but making such claims is weaker than claiming Level 2.
OWASP ASVS – Web Application Edition (Beta) Downloads
OWASP ASVS – Web Application Edition (Alpha) Downloads
OWASP ASVS Alpha (English)
Feedback
Please let us know how your organization is using the OWASP ASVS. Include your name, organization's name, and brief description of how you are using the ASVS. Thanks for supporting OWASP!
We hope you find the information in the OWASP ASVS useful. Please contribute back to the project by sending your comments, questions, and suggestions to owasp-application-security-verification-standard(at)lists.owasp.org. Thanks!
To join the OWASP ASVS mailing list or view the archives, please visit the subscription page.
Project Sponsors
The OWASP ASVS project is co-sponsored by:

|
Click here to see this project's full SoC 2008 status.]
This category currently contains no pages or media.